Five Good Tips For Your Computer Security
Or, well… Actually, it’s about the five absolute dumbest things you can do with an Internet-connected computer. My 'best tips' are really about pointing these out and maybe getting you to do something about them.
(This page is a slightly revised and updated version of one of my old (?) blog posts. However, the information is just as current and relevant today as it was in 2015.)

1
Don’t write ANYTHING (!!) online that you don’t want someone else to find out about!
Whether it’s in emails, a Facebook post, a private message, on a so-called cloud service (online storage), or in a chat, what you write is not confidential. It can very easily—or rather, quite likely—spread without your knowledge and be used in all kinds of ways.
A good example could be a completely personal diary. I would mainly recommend writing one on paper, but if you still want to use your computer, tablet, or phone instead, make sure to save the files locally, meaning on your own device, and preferably encrypted in some form. (For encrypted storage on your computer, see the end of the next point.) You can be as paranoid as you like when it comes to personal and/or secret text, but for normal users, I think some kind of encrypted storage locally on your own computer is a pretty good solution. It all depends on how secret the information you’re saving really is. If it’s, for example, all of your (or your company’s) accounting and financial data, then you need to be extra paranoid. But if it’s just a personal diary, the above—local encrypted storage—should be a fully sufficient method.
(Of course, this applies to any files you don’t want others to be able to see. So don’t put pictures, audio, text, or videos online if you want to keep them private. As for cloud storage, such services can indeed be used to keep backups in case your computer (for example) crashes. My advice, however, is to make sure that files you want to keep private are encrypted in some way before you upload them to the “cloud.” Most cloud storage services are (I think?) encrypted with so-called end-to-end encryption. But here, it really comes down to whether you trust them. If you want to be extra cautious, you should encrypt the files yourself before uploading them.)
See below for tips on different programs for encrypting files or creating an encrypted storage area on your computer.
2
Don’t use the same password for multiple sites or services!
Say you happen to use the same password for your Facebook login as for your email at, say, Gmail. Suppose someone finds out your Facebook password. Not so bad, you might think? Well, it’s not just that people could post things in your name, send personal messages pretending to be you, and ask people you know to do various things. The latter could include asking them for their login details — and if they’re foolish enough to give them, those credentials end up in the hands of someone completely unauthorized.
What’s worse is if you use the same password in several places (for example Gmail): the “hacker” (for lack of a better term) can now use your email for all sorts of things. Not so bad, you might think? But your friends don’t know your email account has been hijacked! They won’t find out because you no longer have access to the account yourself. The hacker has, kind (?) as they are, changed your password without telling you. They now OWN your email! You can of course protect yourself against this scenario and maybe recover your email account, but it’s quite a hassle. The simple “solution” would be to call everyone you know and tell them what happened and that they should ignore any messages coming from your.name@themail.com
But what’s even worse is that the hacker can now calmly and freely read all your past emails (and any that are sent to “you” in the future). Believe me — you don’t want a total stranger to have access to everything you’ve sent and everything you’ve received. And believe me, you have no idea what a hijacked email account (in your name) can cause down the line.
Edit Jan 24th, 2016:
It’s worth mentioning in this context that your (only) password doesn’t necessarily have to leak because you did something foolish. It could be one of the websites you log in to that isn’t handling its security properly. Sometimes it comes out that a site recommends its users to change their password because their database has leaked—or is suspected to have leaked. If you then use the same password for many different sites and services, you’ll have a pretty big job on your hands changing your password everywhere… if you even remember all of them! Just imagine how convenient it would have been if you had done what you should have from the beginning—namely, used completely different passwords for every website, site, and service.
/edit
But how am I supposed to remember all my passwords for maybe a hundred different sites and services online? One way is, of course, to write them down on paper or in a notebook that only you have access to. (Not something I recommend, though.) Another, and perhaps a bit smarter, way is to write them down in a regular text document and save it as an encrypted file, or place it in an encrypted storage area locally on your computer. The point is that you then only need to remember one single password going forward (besides the login for your computer, which should not be the same). You then use this “master password” to access all the others. I myself have previously done this by saving the document in an encrypted zip file. Nowadays, however, I use both an encrypted area on my computer where I can easily store all sorts of private things, and a so-called password manager for all login (etc.) details.
How then? That was the question. Well. The simplest way (?) is to use a free compression program such as 7-Zip, and save the text file in it, with encryption and a password. See this video on YouTube for instructions, or a more detailed explanation in this video. If instead you want to use a probably safer alternative—or at least create a larger encrypted storage space for all sorts of files—I recommend using VeraCrypt (also find out more at wikipedia.org/wiki/VeraCrypt) or possibly TrueCrypt. These two programs are very similar to each other since VeraCrypt is a further development of TrueCrypt. A good instructional video can be found here.
 Edit Jan 24th, 2016:
Edit Jan 24th, 2016:
Everything above, in the last paragraph, is not the best option though. For handling of your passwords and credentials I now strongly recommend that you start using a dedicated password manager program. Personally, I’ve chosen the free and open-source program KeePassXC.
/edit
3
Stop (!!) trusting that your computer isn’t being attacked with malicious code!
So: Install antivirus and firewall programs and make sure they are kept updated and, above all, working. Why? Simply because so much junk is spreading everywhere, pretty much all the time. Unfortunately, you don’t even need to be aware that you’ve been infected until it’s far too late. Anyone who knows what a ransomware is (see the example image below) and perhaps has even fallen victim to it, knows the misery it can cause.
The so-called
*) Instead of starting completely from scratch, it makes a huge difference if you’ve backed up all your important files. (See below for more info.)
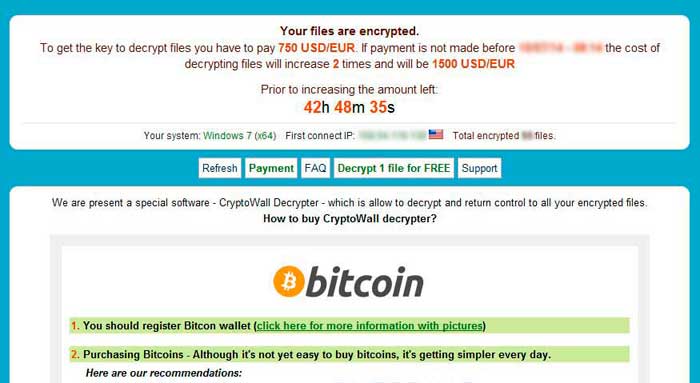 Ransomware is just one form of malicious code that you can be affected by.
Windows computers, which I’m fairly familiar with myself, have basic protection through Windows Defender, and especially the Windows Firewall is quite competent. But when it comes to antivirus programs, I would advise you to install a separate one. Free antivirus programs, however, I would not recommend. Windows Defender is currently more than adequate. Free antivirus programs often mean that you get a number of messages and popups about buying their “better” (?) versions, which of course cost money.
Ransomware is just one form of malicious code that you can be affected by.
Windows computers, which I’m fairly familiar with myself, have basic protection through Windows Defender, and especially the Windows Firewall is quite competent. But when it comes to antivirus programs, I would advise you to install a separate one. Free antivirus programs, however, I would not recommend. Windows Defender is currently more than adequate. Free antivirus programs often mean that you get a number of messages and popups about buying their “better” (?) versions, which of course cost money.
I have myself previously used free antivirus programs (Avast and earlier AVG), but I eventually started subscribing to a paid version (F-Secure), since I noticed that Avast slowed down my internet connection significantly. I stopped using AVG when so many different less relevant messages started popping up (e.g., about buying their paid version) that I finally got tired of it. One thing is important to keep in mind: whichever antivirus program you use, it will not protect you 100%. Very shady websites on the internet are still a risk. And if you tend to just click on and approve anything that seems exciting or looks necessary, then sooner or later you will be hit by some malicious code that manages to get through the protection that even a competent antivirus solution provides.
So, which antivirus software should you install? Go by recommendations, even if they “just” happen to come from reliable websites, like this one. ;)
Update Jan 9th, 2016:
Since you can never be entirely (100%) sure that you won’t be affected by some malicious program—or that your computer’s hard drive won’t fail and simply stop working—I strongly recommend making backups regularly of files you absolutely don’t want to lose. This mainly applies to photos, videos, and documents that you have created yourself and therefore cannot be retrieved from the internet. You can keep backups either in the so-called cloud, meaning on some (encrypted) internet service like Google Drive, Dropbox, or OneDrive. Or you can use an external hard drive and manage your backups with, for example, SyncToy 2.1 from Microsoft (no longer available, but you can search for it if you want). I’ve chosen the latter method with an external hard drive, since hard drives that are inside the computer and thus are always connected can also be hit by viruses such as ransomware. The only disadvantage I see with an external hard drive is if you suffer a fire or burglary at home and you keep it stored there. In that case, it could also be “gone.”
/end update
4
Don’t believe everything you read, and don’t click on everything you can click on!
How can you be sure that none of your friends’ Facebook or email accounts have been hacked? How can you be sure that a link that “they” send you doesn’t lead to something harmful or something that’s of absolutely no use to you?
So-called phishing emails are just one type of email you might come across. Phishing, in short, means you receive an email (or a chat message) that looks like it comes from a friend asking you for something. Most commonly, though, a phishing email looks like it comes from your bank or, for example, Gmail, asking you to follow a link in the email to log in (to fix something “important”). But instead of logging in, you’ve just sent your username and password to a malicious cybercriminal. Notice that both the email and the website you’re directed to can look, and often do look, exactly like they come from the real service. But they are simply copies that some crook is controlling.
Does it look suspicious? Don’t click!! Does the email seem unusual for coming from your “friend”? Don’t click!! Do you not recognize the style, language, or layout of the email? Don’t click!!
These are very important basic rules, and if you have any doubts, contact your friend some other way to find out if it’s really him or her who sent it. And if it’s an institution, such as your bank or email provider, then go there manually, so to speak, (not via a link in a suspicious email) and check directly if there’s something you need to or should deal with.
5
Stop believing that you're (probably?) not a "target"!
- Do you have money in the bank? If the answer is yes, then you are a target. (Or at least you could be a target.)
- Do you have hard drive space on your computer or other storage? If so, then you are a target.
- Do you have an internet connection? Maybe even ultra-fast broadband? Then you ARE a target.
In short, it’s not about what you believe or think, but about what the criminals consider profitable or useful. And it doesn’t all have to be about money. Your computer and your internet connection can be exploited for all sorts of things you would hardly want to be associated with—and without you noticing anything suspicious. For example, your storage space could be used as a temporary cache for everything from terrorist propaganda, bomb-making recipes, and contacts, to child pornography. Or your broadband could be used to carry out large-scale attacks against others connected to the internet, in so-called denial-of-service attacks.
So, not everything has to be about money. Crooks and criminals online can have all sorts of different motives and goals. Money is of course a big factor, and an increasingly important one these days, now that yesterday’s annoying and mischievous “hackers” have instead become outright cybercriminal individuals (or are part of a criminal organization). And as I’ve described, it can just as well be about your computer becoming a “service” that criminals exploit (without thanking you, of course) for the “privilege” of using it.
On the next page, I’ll go through the basics of PGP encryption.
